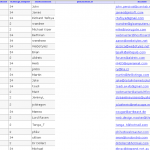
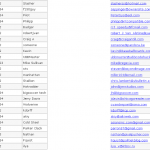
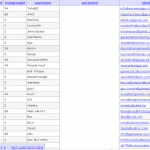
As news of the data breach at vBulletin.com and vBulletin.org made mainstream media news, it has left a lot of system administrators and forum administrators extremely nervous since almost one million usernames, emails, and passwords have been compromised.
Possible 0-Day?
Several news outlets have reported there is a Zero Day Remote Code Execution vulnerability affecting all iterations of vBulletin 4.x and vBulletin 5.x series that allows an attacker to execute arbitrary code on the server remotely.
The exploit is being sold for roughly $7,000.00 USD, payable only in virtual currencies Bitcoin and WebMoney. According to Brian Krebs at KrebsonSecurity, at least one individual has made the purchase.
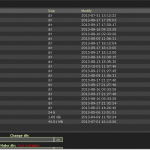
As added proof of concepts, the following screenshots of the vBulletin database, sever shell, and tables have been released. We can confirm that the database information is indeed legitimate.
Historically when an exploit is sold, the exploit itself is, for the most part, tested and validated as a working exploit.
Several vBulletin forum communities, including the DEF CON Conference Forums, have been taken offline because of the vBulletin 0-Day in the wild and have chosen not to return until a patch is released.
Other forum communities have begun the massive task of migrating away from vBulletin as the issue appears to be growing exponentially.
Earlier yesterday, when confronted by vBulletin customers, it was unveiled that the attackers had access to the Magento customer database, which gave attackers access to customer billing addresses. Whether the access was utilized or not is still up for debate, however logs indicate that they were not accessed.
vBulletin Solutions, a wholly owned subsidiary of Internet Brands, denied the allegations of a real 0-day threat to vBulletin.
“Given our analysis of the evidence provided by the Inject0r team, we do not believe that they have uncovered a 0-day vulnerability in vBulletin.
“These hackers were able to compromise an insecure system that was used for testing vBulletin mobile applications. The best defense against potential compromises is to keep your system running on the very latest patch release of the software.” wrote Wayne Luke, vBulletin Technical Support Lead.
Whether this attack is related to the MacRumors.com data breach earlier in the month is still being debated among vBulletin customers given that MacRumors was running an older version of vBulletin.
Prepare for an attack?
For websites currently utilizing vBulletin, we recommend that all web application firewalls and defenses for servers hosting vBulletin be tuned to a much higher setting until the situation resolves. Server administrators are also encouraged to enable verbose logging to help with the incident response process.
Alternatively, vBulletin customers may choose to seek an alternative forum solution of their choosing.